Cisco Spaces OpenRoaming Runbook (Cisco Validated)
OVERVIEW
This Cisco validated runbook is designed only as a follow on from the Spaces OS Runbook. If you have not completed that runbook yet, please go back and ensure that the deployment has been validated against that before continuing here.
With the standard expectation of users to always be connected to the internet no matter where they are, it is paramount that users can be connected securely and seamlessly. Wi-Fi onboarding allows users a frictionless onboarding experience and a seamless handover when roaming between cellular and Wi-Fi.
OpenRoaming enables secure, seamless, and automatic network connectivity by eliminating tedious Wi-Fi guest onboarding processes and the risk of connecting to rogue SSIDs. This is especially helpful for a mobile device user trying to access the internet because OpenRoaming removes the need to choose between multiple SSIDs, or enter insecure, shared credentials on poorly designed captive portals.
This runbook will look at OpenRoaming to onboard customers. For information about integrating with Carrier Offload with Partner Apps (such as AT&T Auto-Attach), please refer to Annex A: Carrier Offload with a Partner App (AT&T Auto-Attach)
SUPPORT AND ONBOARDING
Please follow the link below to find out about the different ways to get support for Cisco Spaces.
PREREQUISITES
This runbook should only be used as a follow on from the Spaces OS Runbook. All the prerequisite steps are covered in the Spaces OS runbook and should be completed before progressing here.
Namely, OpenRoaming requires the following prerequisites met:
An active Cisco Spaces account.
A Cisco wireless network. Both controller-based (Cisco AireOS or Cisco Catalyst wireless controller) and cloud-based (Cisco Meraki) networks are supported.
Add the wireless network to your Cisco Spaces account.
For controller-based architecture, the Cisco Spaces Connector must be used.
For Cisco Meraki networks, add the Cisco Meraki account to your Cisco Spaces account.
For Cisco Meraki networks, an SSID for OpenRoaming must be configured in the Meraki dashboard first. Refer to Appendix: Setup OpenRoaming SSID in Meraki Dashboard
OpenRoaming Prerequisites
Network Components
C9800 WLC*1 | -16.12.1 or above |
AireOS WLC* | -8.3 or above supported |
Meraki | -Supports OpenRoaming -Minimum MR 31.1.6 needed -Admin access required for Meraki Account to activate SSID for OpenRoaming -At least one unconfigured SSID on Meraki Dashboard in “Disabled state” -Ensure OpenRoaming SSID has strong encryption e.g “WPA2 Only” or “WPA3” |
Cisco Spaces Connector2 | -Highly Recommended version 3.x -Minimum version 2.3.2 or above. Starting December 2023 Connector 2.x entered software maintenance mode. Security updates will continue through June 2024 and support for critical bug fixes will continue through October 2024. ( EoL Notice ) |
CMX Tethering | Not Supported |
AP Support | All 9100 Series Access Points Catalyst Wave 1 and Wave 2 Access Points All MR Wi-Fi 5 wave 2, Wi-Fi 6 and Wi-Fi 6E APs |
1 Embedded Wireless Controller (EWC) on Catalyst 9100 and the Embedded Wireless on Catalyst 9000 switches are NOT supported.
2 Cannot be configured with HTTP/HTTPS proxy enabled.
See WLC release notes for supported APs per release
OpenRoaming Client Matrix
Device Support | -Samsung Devices: Android 10 or higher -Google Pixel: Android 11 or higher -Apple devices running iOS 13.3 or higher |
OS Support | -Apple devices running iOS 13.3 or higher -Android phones running Android 9 or higher |
Cisco Spaces SDK | -iOS 13.3 or higher -XCode version 12 or higher -Android 9 or higher |
Service Providers (today) | -T-Mobile -AT&T -Comcast |
SSID broadcasting must be enabled for OpenRoaming to function
IMPLEMENTATION
To complete these steps, an admin will require read/write permissions within Spaces for OpenRoaming and DNA Spaces, as well as read/write access to Meraki Dashboard and/or WLC, and read access to connector for verification.
With the prerequisites covered, implementing OpenRoaming requires four main steps:
Create an OpenRoaming Profile
Enable Hotspot Connector
Configure Network Controller
Configure the OpenRoaming SSID
Each of the main steps will be discussed.
Create an OpenRoaming Profile
An OpenRoaming profile contains information about the network SSID and specifies which user identities are allowed to access the guest network. You can also configure carrier offload in the OpenRoaming profile.
To create an OpenRoaming profile, the following substeps need to be performed:
Substep 1: Set Access Policy
Substep 2: Configure an SSID
Substep 3 (Optional): Configure Carrier Offload
Substep 4: Review and Confirm Settings
Click here for a video guided demo
Set Access Policy
Set your policy on who can access your OpenRoaming network.
Go to OpenRoaming app within Cisco Spaces Dashboard.
Access the OpenRoaming App
Or alternatively, through the side-menu by clicking the Dashboard drag-down.
Click on Setup. If this is the first time that you are setting up OpenRoaming, when you click Setup, a Terms and Conditions dialog box is displayed. Click I Agree to proceed.
In the OpenRoaming Profiles section, click Create OpenRoaming Profile.
The Create an OpenRoaming Profile configuration wizard is displayed.
Click Proceed.
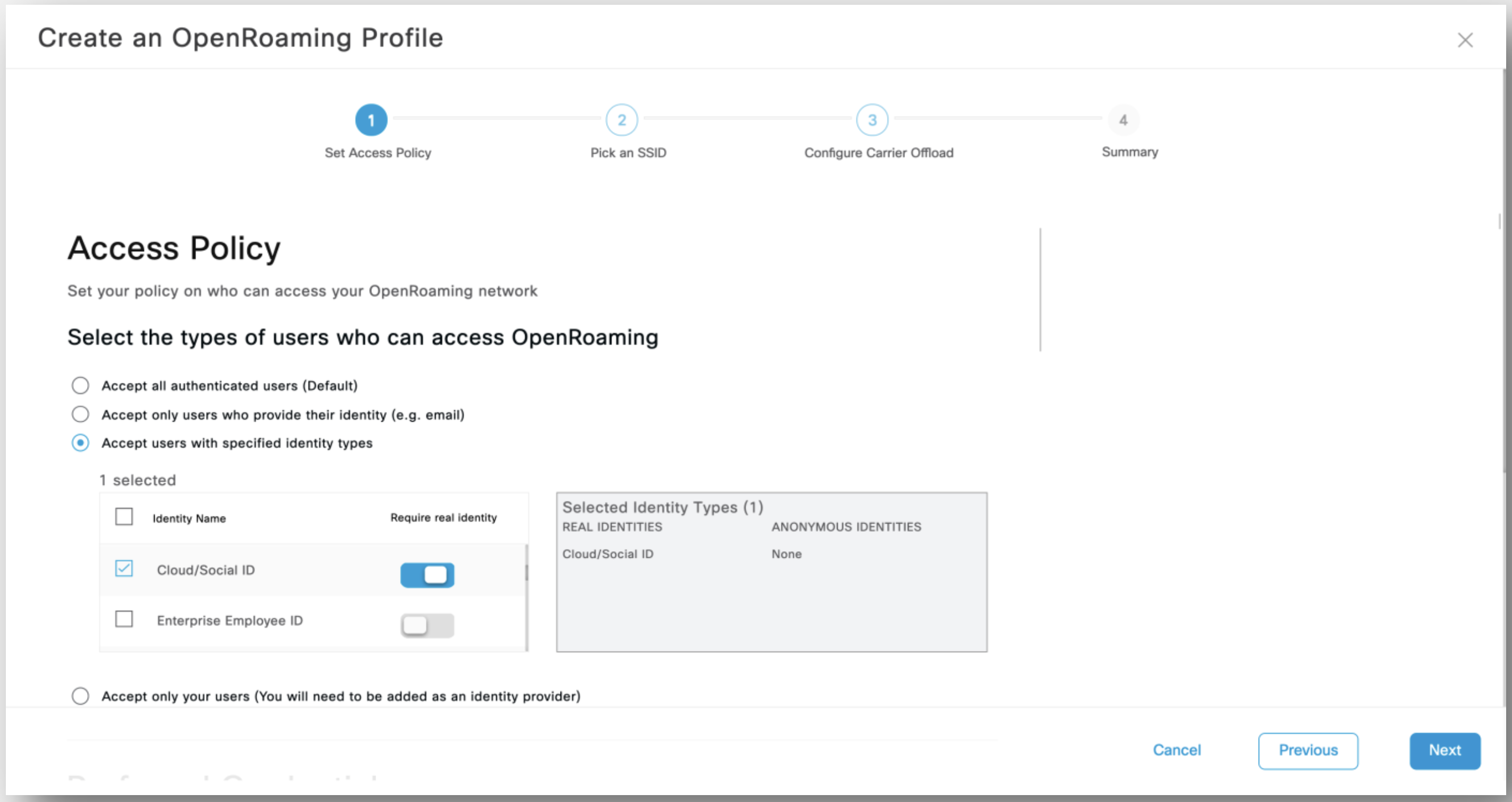
Under Access Policy, specify who can access your OpenRoaming network. Select the types of identities that can access the OpenRoaming network as well as if real identities are required.
The options available are:
i) Accept all authenticated users: This is the default option.
ii) Accept only users who provide their identity: An example of an accepted identity is a real identity, such as an email ID.
iii) Accept users with specified identity types: Choose the desired identity types from the list that is displayed. Enable the Require real identity knob if you want users to enter their real identities. The identity types chosen here is displayed adjacent to their real or anonymous identity settings, in a table next to this list.
Set Access Policy
iv) Accept only your users: If you choose this option, you will need to be added as an identity provider.
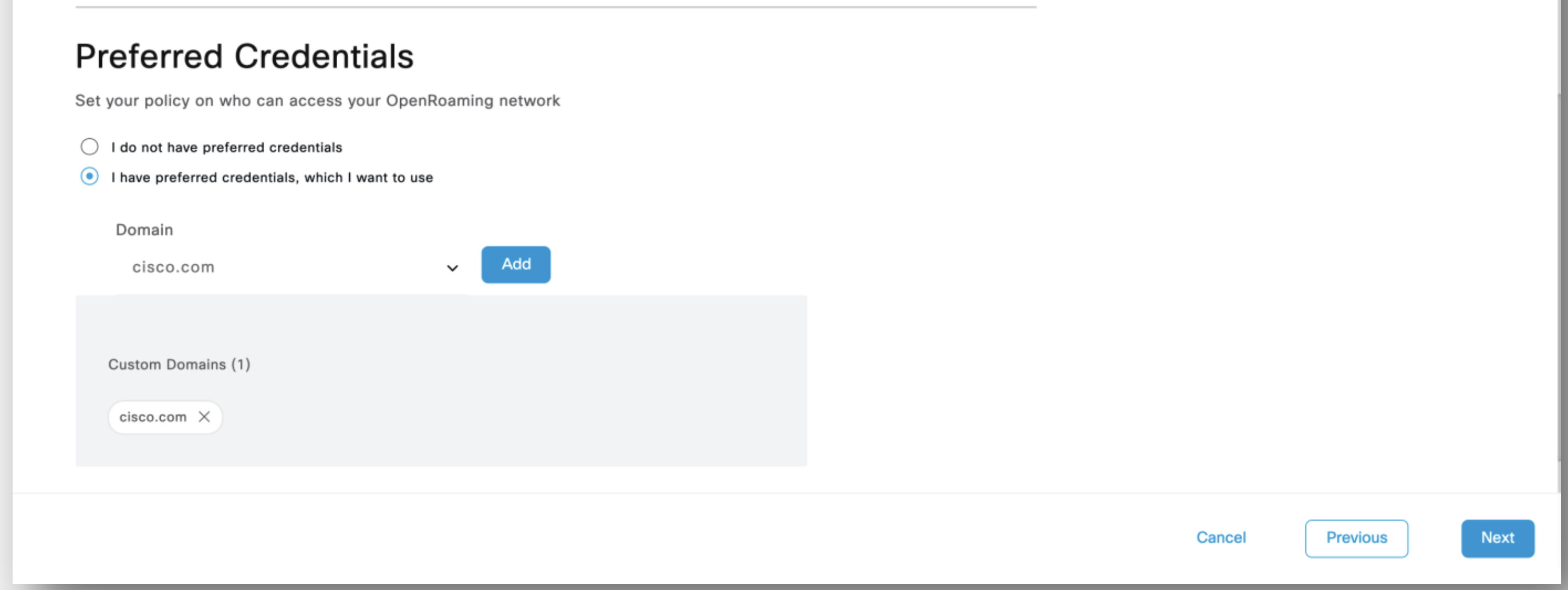
Under Preferred Credentials, choose the desired option from those listed below by clicking the corresponding radio button. This option will set your policy on who can access your OpenRoaming network:
i) I do not have preferred credentials
If you have selected Accept only your users in the Access Policy section, this option will be disabled.
ii) I have preferred credentials, which I want to use: If you choose this option, you must select a domain from the list of domains that are displayed or click Add a Custom Domain.
Set Preferred Credentials
Click Next.
The SSID Details window is displayed.
Configure an SSID
Enter the SSID details for this OpenRoaming Profile - this is a secure SSID different from your guest SSID.
In the SSID Details section, enter the SSID name in the corresponding field. This is the SSID that will be broadcast for OpenRoaming.
If the name that you enter is an existing SSID, ensure that the SSID name is an exact match of what is in the network.
(Optional) In the Advanced section, you can choose among the following options by clicking the corresponding radio button:
i) Default Status: Choose between Enable or Disable by clicking the corresponding radio button. The default option is Enable.
ii) Fast Transition (802.11r): Choose between Adaptive, Enable or Disable by clicking the corresponding radio button. The default option is Adaptive.
802.11r is to significantly reduce the length of time that connectivity is interrupted between a mobile device and Wi-Fi infrastructure.
When 'Enable' is selected, the controller allows all clients to use Fast Transition, even if they don't support it.
The 'Adaptive' option enables Fast Transition only for clients that support it. The controller will dynamically determine which clients are Fast Transition capable and allow them to use Fast Transition. Clients that do not support Fast Transition will fall back to regular reauthentication processes.
The Create an OpenRoaming Profile configuration wizard is displayed.
Click Next.
The Carrier Offload window is displayed.
Configure Carrier Offload (Optional)
You can leverage your Wi-Fi network to provide voice and data services to mobile carrier subscribers on your Wi-Fi network. This configuration is optional.
Ensure that the Settlement Provider is already configured previously. See below.
Before you configure carrier offload, ensure that the following prerequisites are in place:
You must have an existing relationship with a mobile carrier or service provider.
You must have configured the settlement provider with the mobile carrier or service provider.
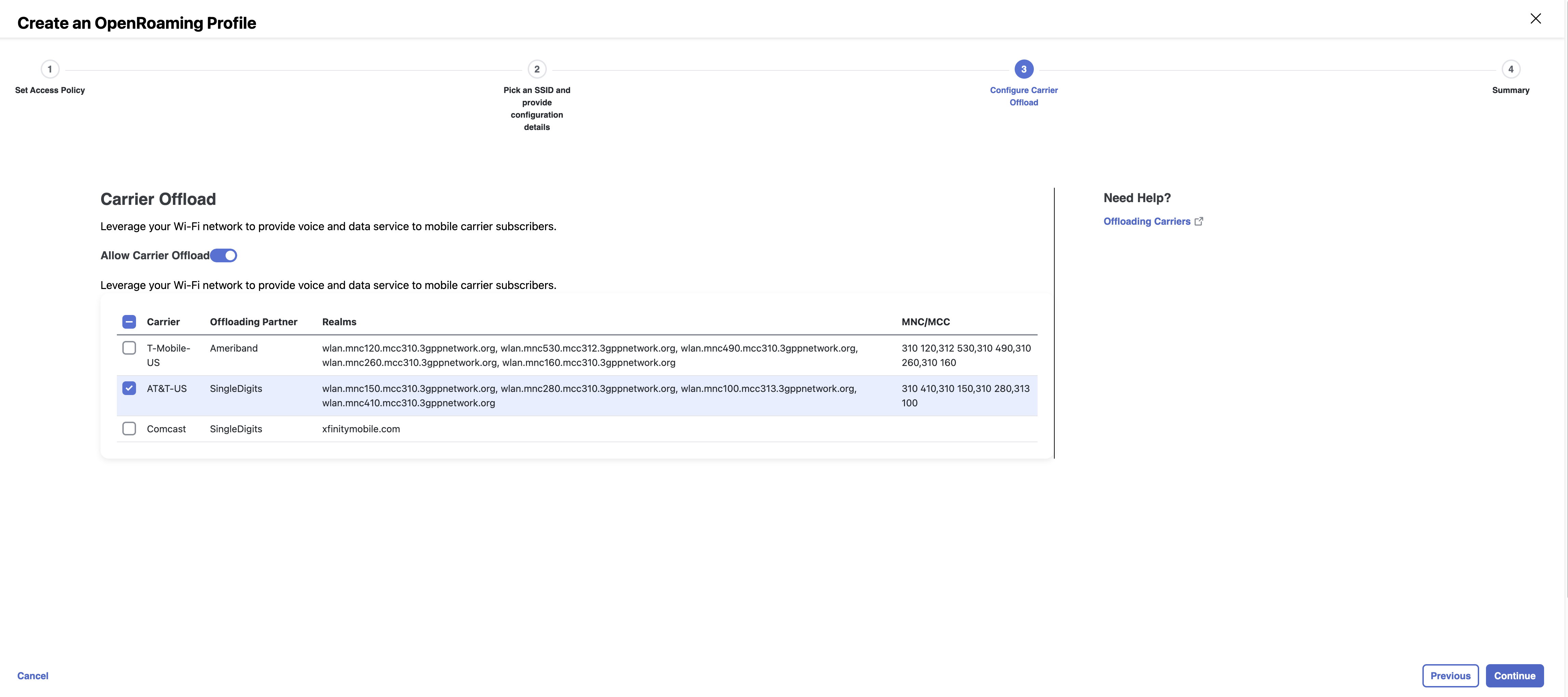
Use the Allow Carrier Offload knob to enable the Carrier Offload settings.
A table listing the various carriers, along with their corresponding details such as the Offloading Partner, Static Routing, Realms, and MNC/MCC settings, is displayed.
Based on your existing relationships with various carriers, you can either select from the carriers that are available in the table or click Add Custom Carrier to add carriers of your choice.
If you have not configured a carrier, or if you click Add Custom Carrier, you must visit the Cisco Spaces Partner App Center to first activate the offloading partner. Contact your carrier offloading partner for specific information that has to be entered in the custom fields. As an example, refer to Annex A: Carrier Offload with a Partner App (AT&T Auto-Attach).
If AT&T is selected as the carrier for Carrier Offload, the dashboard will alert that you must activate this option explicitly through the AT&T Auto-Attach Partner app. This alert has been added since AT&T has mandated that all customers must activate their partner app before they began accepting AT&T users at the venue.

Refer to Annex A: Carrier Offload with a Partner App (AT&T Auto-Attach) for more information about activation.
Click Next.
The Review Your Configuration window is displayed.
Review and Confirm Settings
Review and confirm the OpenRoaming profile configuration.
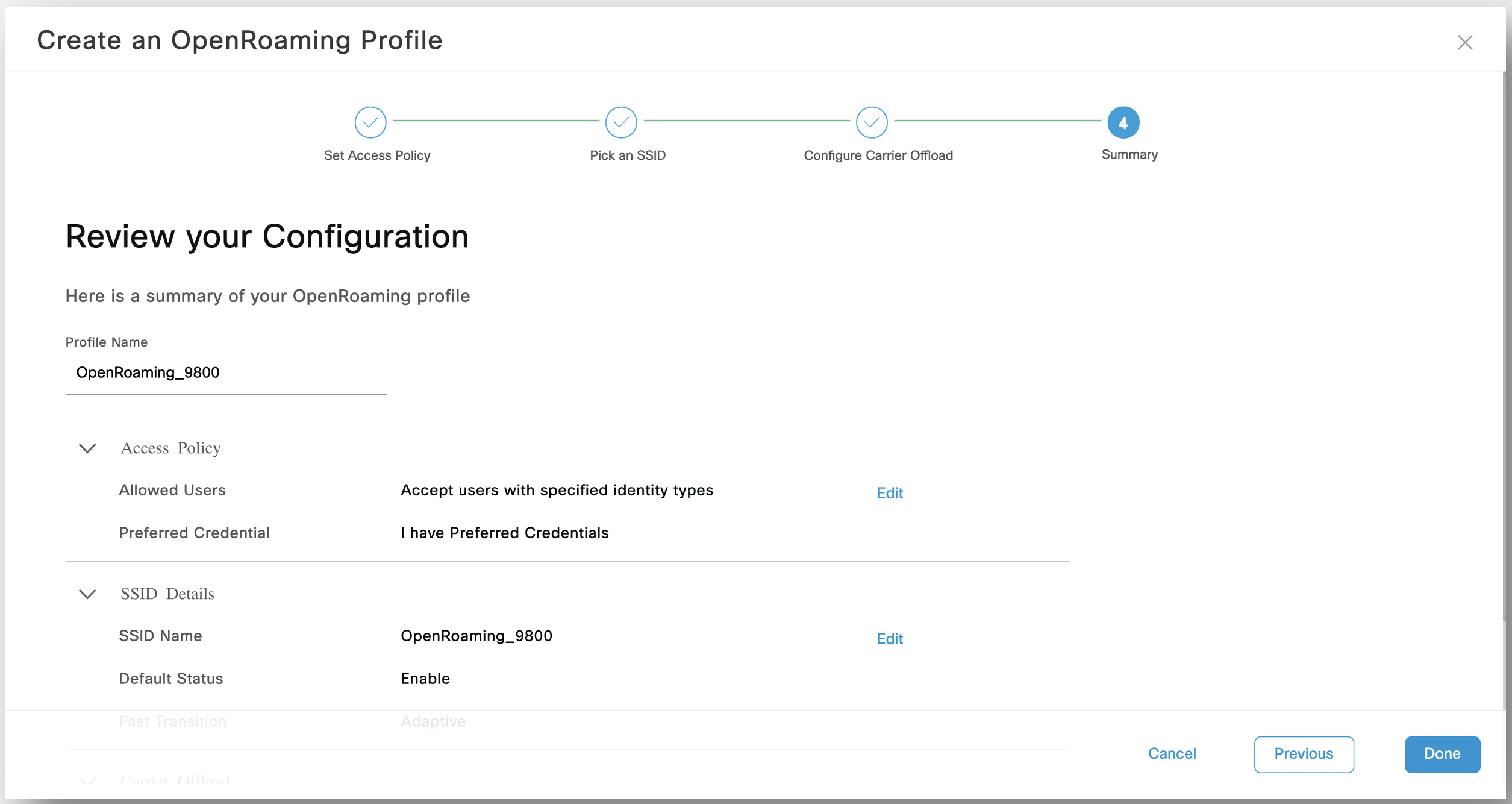
After you have configured the access policy, SSID, and the optional carrier offload, you can review your OpenRoaming profile configuration and modify it if required before saving these settings.
In the Review Your Configuration window, verify the settings and do one of the following:
By default, the OpenRoaming profile name is the same as the SSID name. You can choose to retain the OpenRoaming profile name as the SSID name or modify the profile name.
i) If you are satisfied with the configuration, proceed with the next step by clicking Done.
ii) If you have to make changes, click the Edit link next to the section whose configuration has to be modified and make changes. Continue to click Next until you arrive at the Review Your Configuration window. On successful modification of the OpenRoaming Profile configuration, proceed with the next step by clicking Done.
Click Done to complete the creation of the OpenRoaming profile.
A success message appears briefly, and a confirmation window is displayed.
Review your Configuration

Confirm Profile Created
Enable Hotspot Connector
Enable a Hotspot on the Cisco Spaces Connector (Cisco AireOS or Cisco Catalyst Network)
This step will allow you to enable a Hotspot on the Cisco Spaces Connector for Cisco AireOS or Cisco Catalyst Network. This is needed to add OpenRoaming functionality.
A Hotspot Connector is not needed for Meraki. This functionality is handled via APIs to Meraki cloud.
If using Meraki, proceed to the Step 3: Configure Network → Configure Cisco Meraki Network
When you add a hotspot on the Cisco Spaces Connector, it leads to the installation of a new docker. You can enable a hotspot on the Cisco Spaces Connector either during the initial configuration of the connector or later using the procedure outlined here.
A Cisco Spaces Connector should already have been configured by following the prerequisite Spaces OS runbook. In which case, you can see it listed in the Hotspot-enabled Connectors section on the OpenRoaming Setup window.
Enable Hotspot on Cisco Spaces Connector 3.x
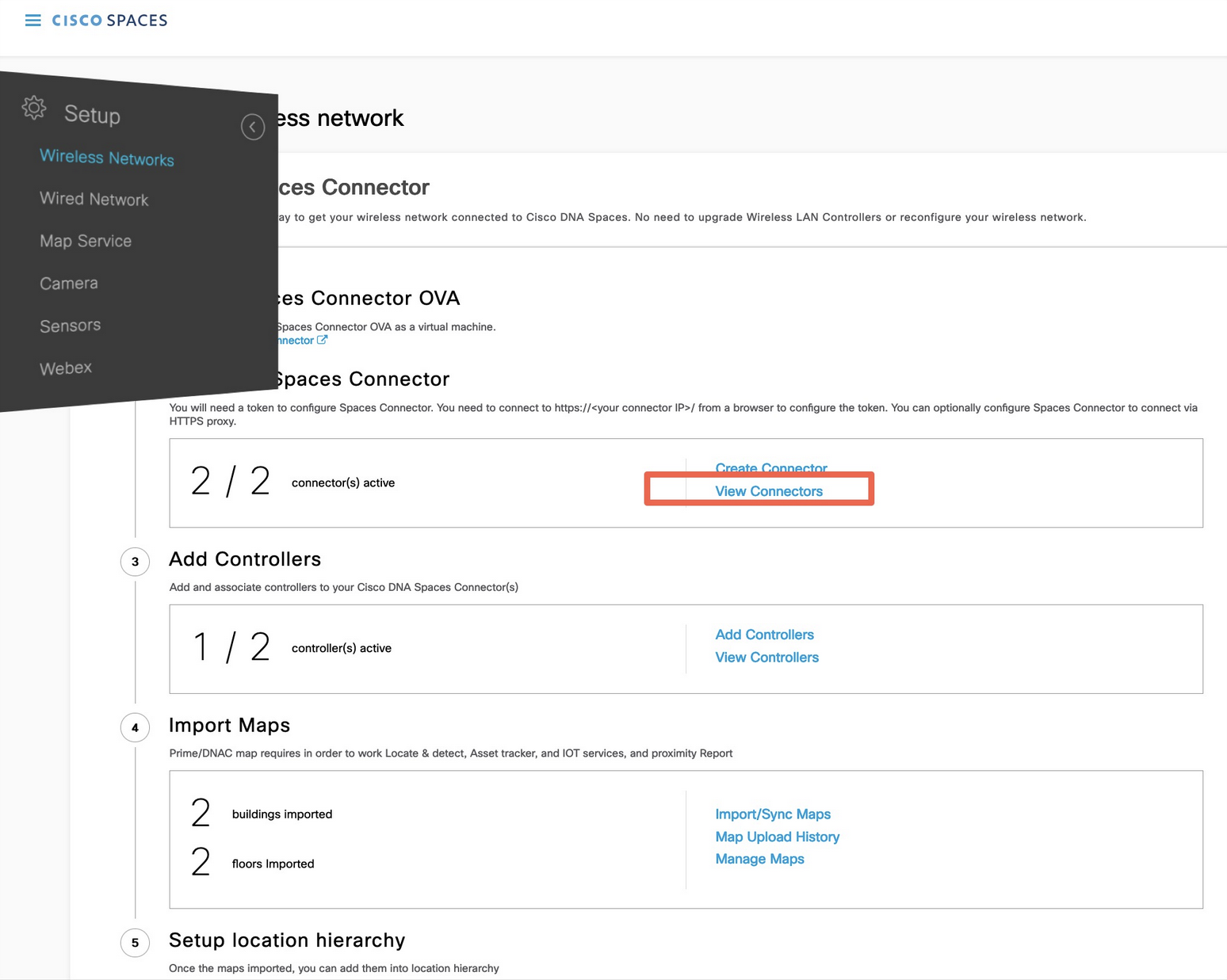
In the Cisco Spaces dashboard left navigation pane, click Setup and choose Wireless Networks.
In the Connect your wireless network window that is displayed, go to the Step 2 area and click View Connectors.
View Connectors
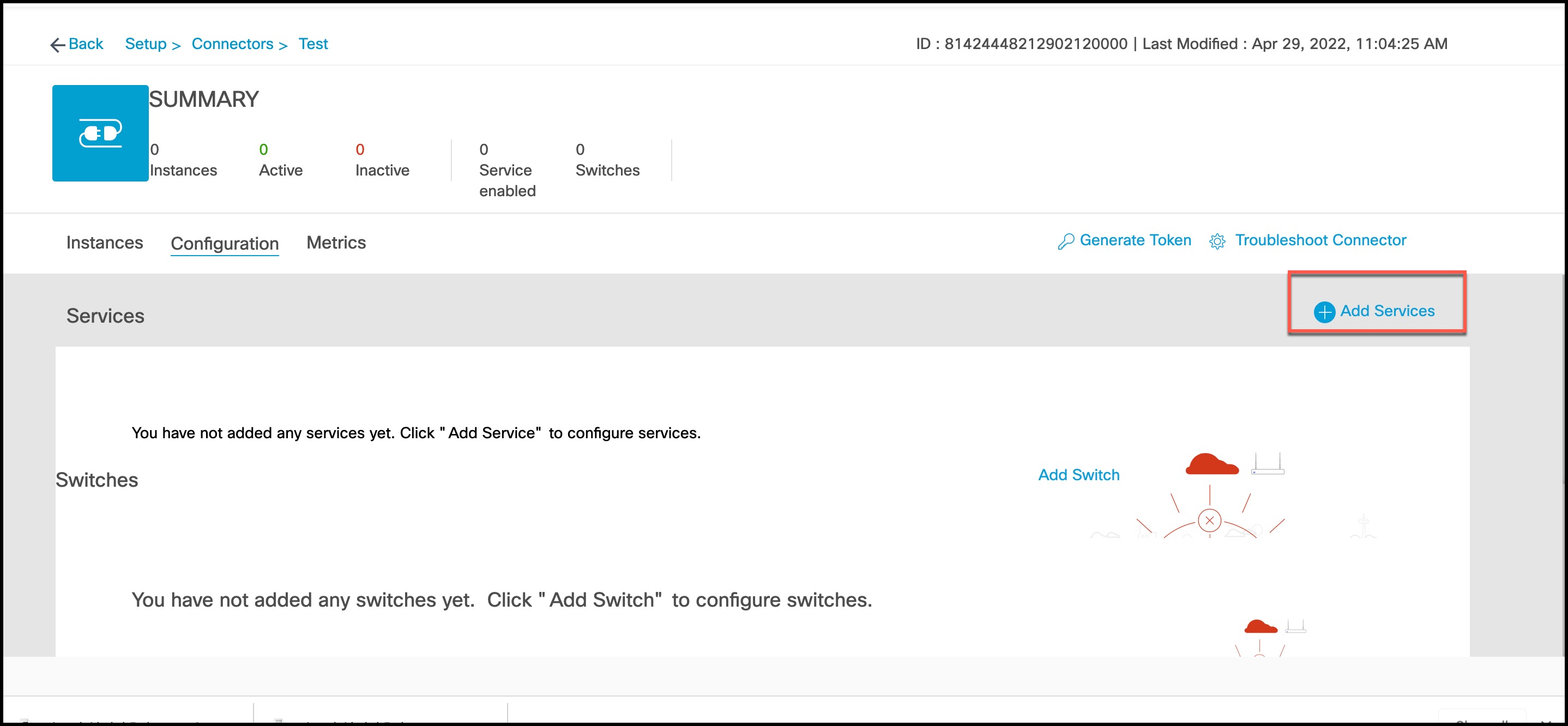
In the connector details window that is displayed, choose a connector and click Add Services.
Add Services
In the Add Service window that is displayed, choose hotspot and click Add.
In Services, Service Manager is added by default.
In the Connector Details window, you can see that the number of services enabled has increased.
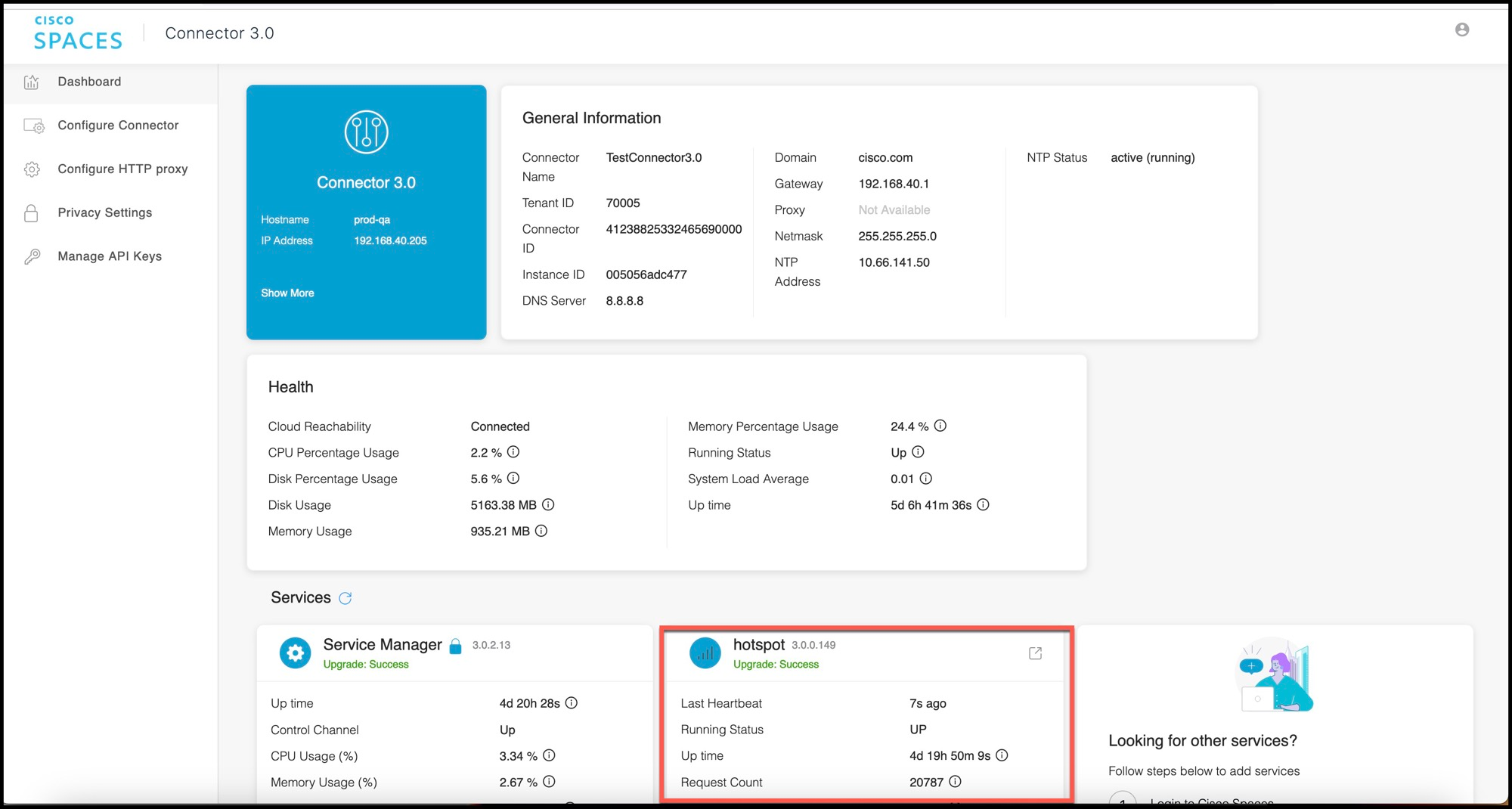
Hotspot Service
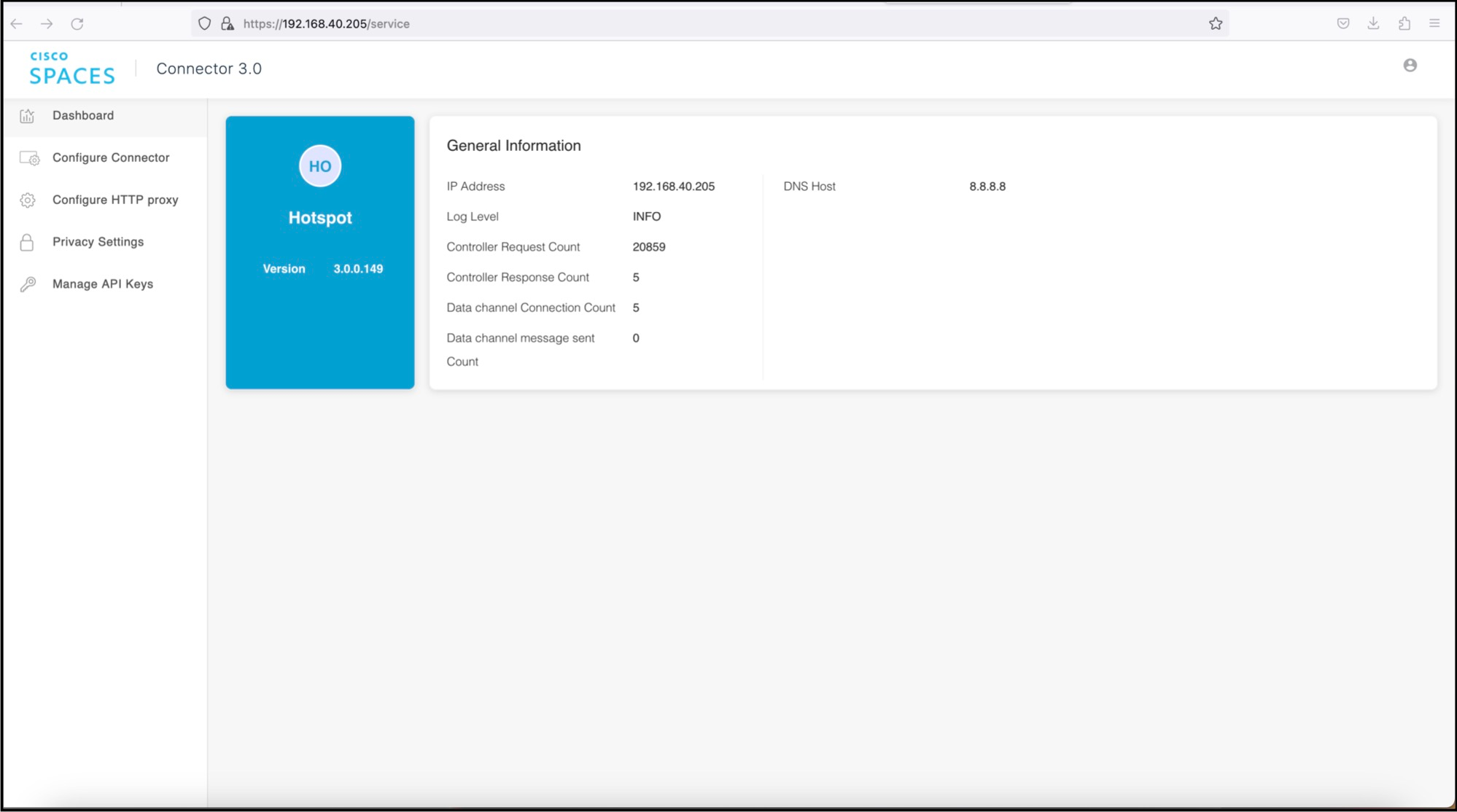
Hotspot Service details
Configure Network
Depending on your wireless network, follow the corresponding procedure to associate an OpenRoaming profile with the controller and configure the network:
Configure Cisco AireOS or Cisco Catalyst Network
Before you configure the Cisco AireOS or Cisco Catalyst wireless network, you must configure the SSID and AAA policy.
In the OpenRoaming window, click Set Up OpenRoaming or choose
 > Setup.
> Setup.
The OpenRoaming Setup page is displayed.
If you have completed the OpenRoaming Profile configuration, click Continue OR Setup in the configuration wizard to proceed.
In the Network configuration section, under the AireOS/Catalyst controllers tab, a list of all the Cisco AireOS and Cisco Catalyst series controllers appears with details such as the Controller status and associated Connectors.
Under Network configuration > AireOS/Catalyst controllers, in the Action column, click the settings
 icon corresponding to the controller you want to configure.
icon corresponding to the controller you want to configure.The Configure Controller window is displayed.
Under Generate Configuration, select the OpenRoaming profile from the drop-down list.
If a non-default policy profile or policy tag is used, you must copy only the Access Network Query Protocol (ANQP) server settings and apply it to the wireless policy profile. Ensure that the policy tag uses the WLAN configured for OpenRoaming, and is mapped to the configured wireless policy profile.
Click Continue.
Choose the controller type between AireOS and Catalyst 9800.

Select the required Controller for your network
In the WLAN ID field, enter the exact WLAN ID that you have configured on your AireOS or Catalyst 9800 Controller.
Click Show Configuration.
Select the either Catalyst: (17.2.1/17.3.1) (for IOS XE versions 17.2.1 or later) or Catalyst: (16.12.1/17.1.1) (for IOS XE versions earlier than 17.2.1)
The generated CLI configuration is for the Hotspot OpenRoaming ANQP server.
The generated configuration assumes the default Wireless Policy Profile and Policy Tag will be used. In deployments with the defaults being used, the entire configuration can be used.
Otherwise, if using a different Wireless Policy Profile and Policy Tag, copy only the OpenRoaming HotSpot ANQP server settings as highlighted below.
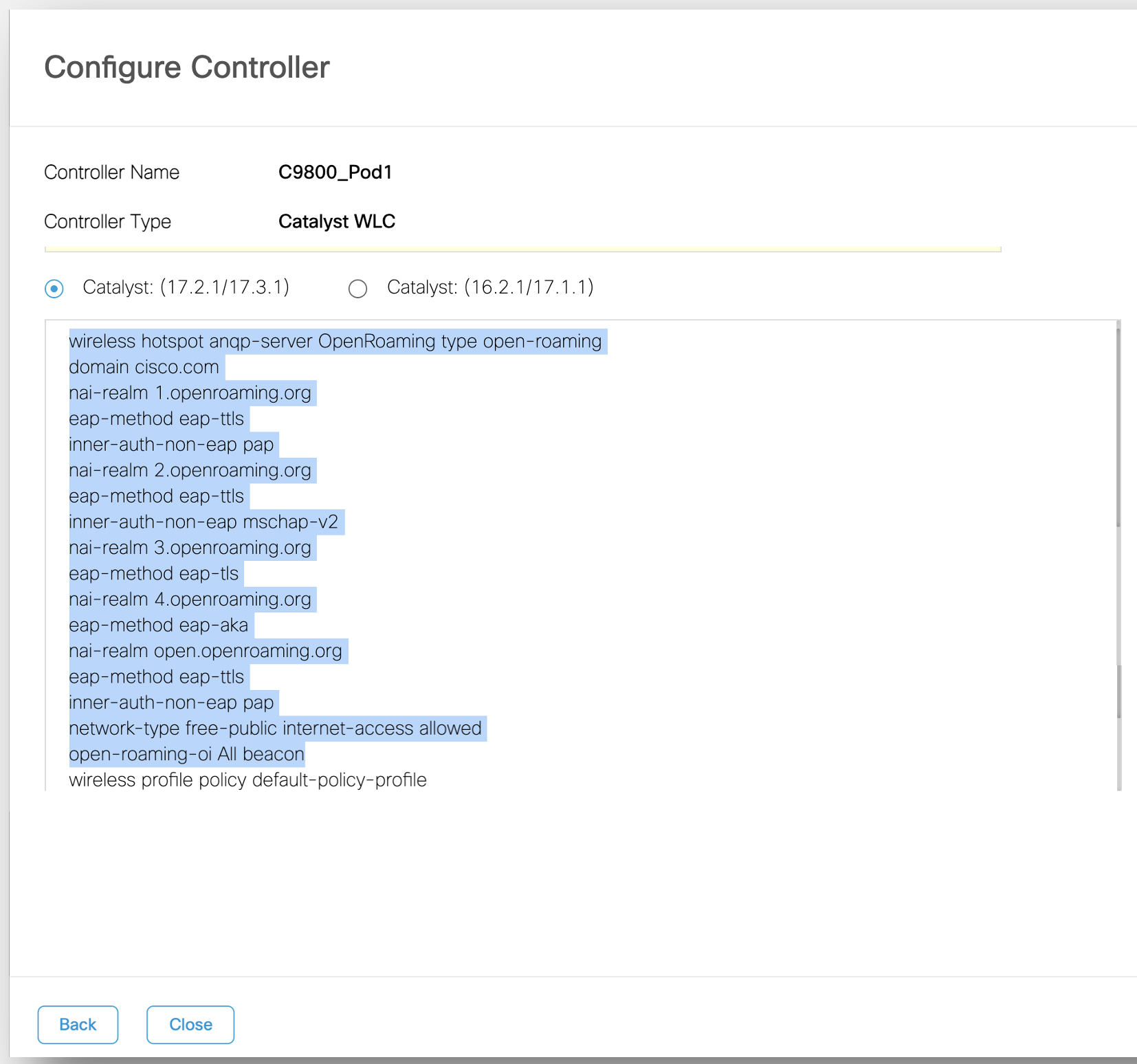
If using non-default profiles, select as above.
Paste the selected OpenRoaming profile configuration in the Cisco AireOS or Catalyst controller CLI.
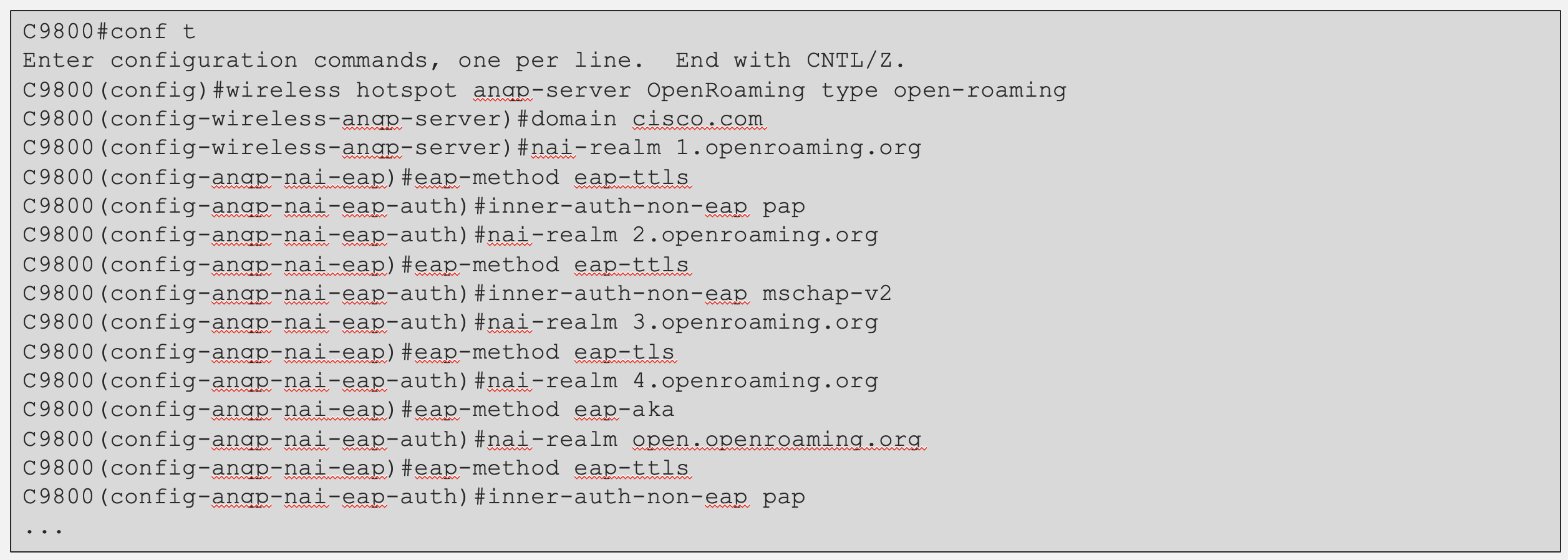
Click Close.
The OpenRoaming Setup window is displayed.
To configure the ANQP server manually on the 9800 Controller or to use non-default Wireless Policy profile and Policy Tag, refer to this video: https://www.youtube.com/watch?v=XsD6e6F6u4k
Configure Cisco Meraki Network
To use OpenRoaming on your Cisco Meraki network through Cisco Spaces, your network must meet the following prerequisites:
All access points in the Cisco Meraki network need to be on R31.1.6 or later versions of the Cisco Meraki firmware.
There needs to be at least one unconfigured SSID and it should be disabled initially.
Contact the Cisco Spaces Support team to enable the feature flag to activate OpenRoaming in your Meraki account.
If you do not meet one or more of the above prerequisites, you can manually activate OpenRoaming on your Meraki network by installing a Cisco Spaces Connector. For more information, see the Cisco Spaces Setup Guide for OpenRoaming.
Configuration of Cisco Meraki networks that use templates is not supported.
In the OpenRoaming window, click Set Up OpenRoaming or choose
 > Setup.
> Setup.
The OpenRoaming Setup page is displayed.
In the Network configuration section, click the Meraki Networks tab.
Click Set Up.
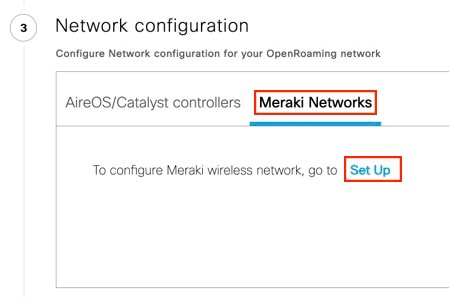
The Configure OpenRoaming for Meraki window is displayed.
For information on configuring a Cisco Meraki network, go to the Cisco Spaces Configuration Guide.
Choose an organization from the drop-down list.
Click Next.
Choose the Cisco Meraki networks for which you want to enable OpenRoaming. This step is not service affecting for the existing SSID(s).
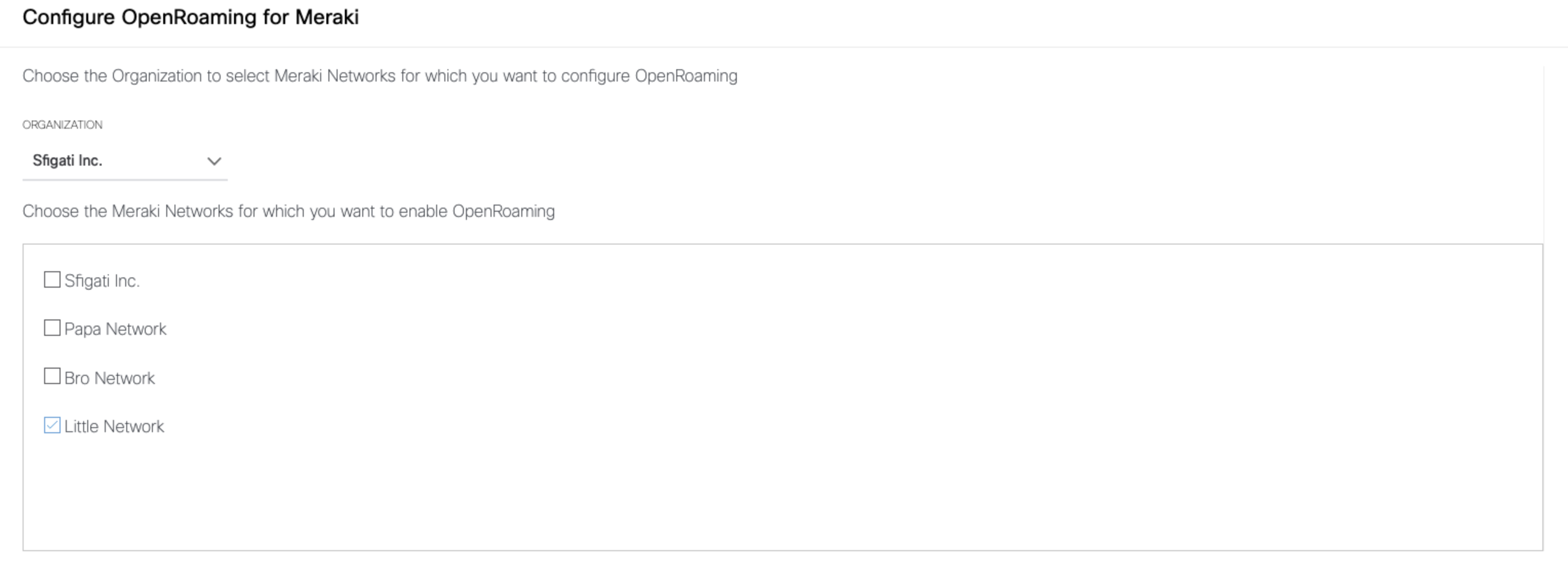
You can select multiple networks from the list.
Click Next.
From the drop-down list, select the OpenRoaming profile that needs to be applied on the Cisco Meraki network.
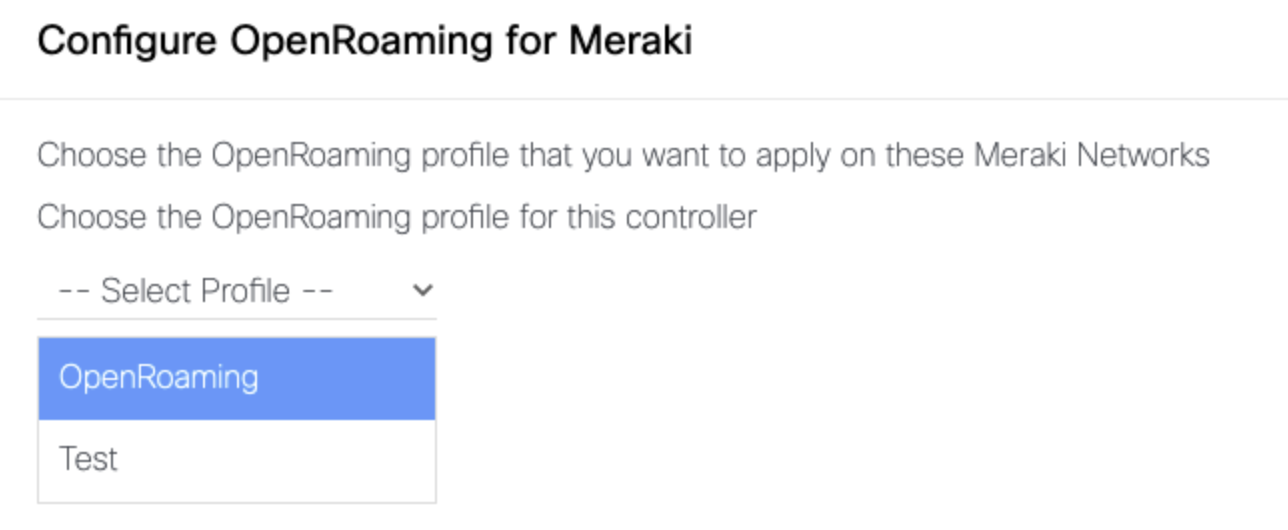
Click Next.
Review the Configuration Summary.
If you would like to make any changes, click Back to navigate to the previous windows.
Click Configure to complete configuration of the OpenRoaming profile on the chosen Cisco Meraki networks.
The OpenRoaming Setup page appears with a success message. Under the Meraki Networks tab, a confirmation message is displayed along with the count of Cisco Meraki networks configured with OpenRoaming profiles.
Setup SSID in Meraki Dashboard
Go to https://meraki.cisco.com
Log in to the application using the login credentials of your Cisco Meraki account.
Click the Cisco Meraki Organization in which you want to enable the SSIDs, and choose the required network.
Choose Wireless > Configure > SSID to configure the SSID.
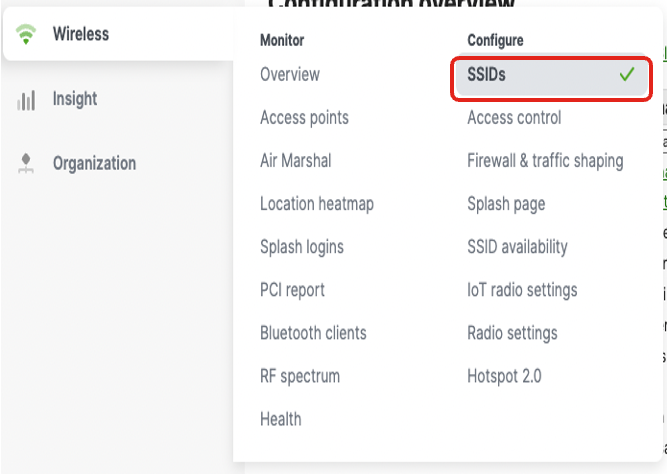
Choose Wireless > Configure > Access Control to rename the SSID and configure SSID-related attributes. Enable the SSID after renaming it.

This same SSID name is used to configure OpenRoaming in Spaces Dashboard. They must match!
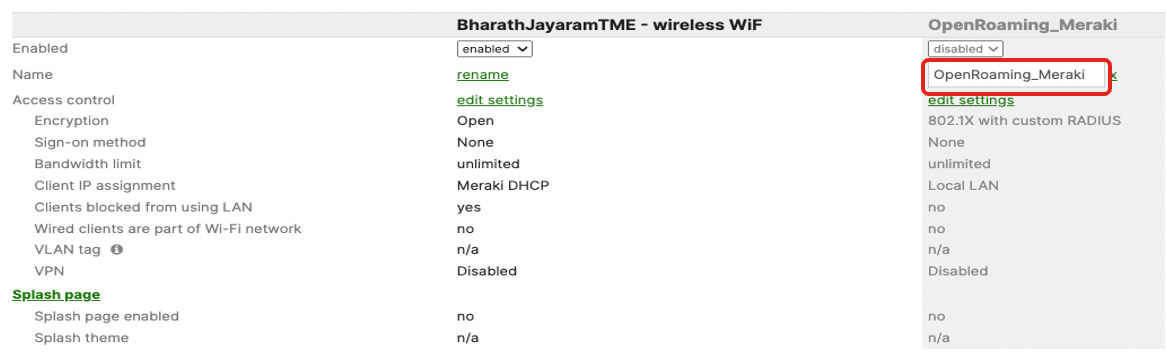
Compare with the SSID name configured in Cisco Spaces OpenRoaming profile to confirm matching names:
Choose the appropriate Radius security on the Access Control page.
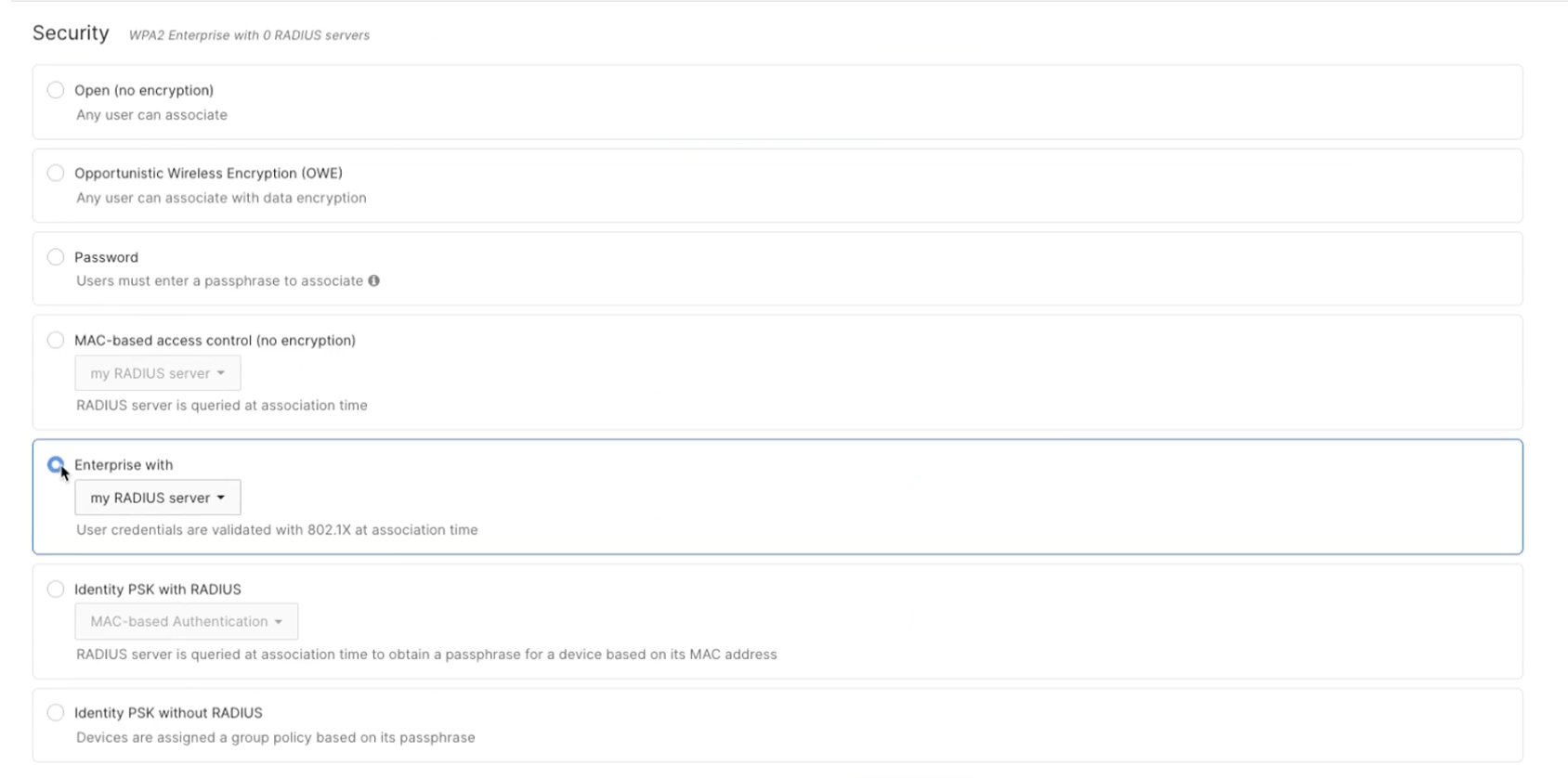
Choose a strong encryption - either WPA2 or WP3.
Some clients might refuse to connect to SSIDs using OpenRoaming when configured with weak encryption methods (e.g., WPA1 or 'WPA1 and WPA2'). Please ensure the SSIDs are configured with strong encryption, such as 'WPA2 Only' or 'WPA3', under Wireless > Configure > Access Control, in the 'WPA encryption' section.

Choose None (direct access) in the Splash page settings.
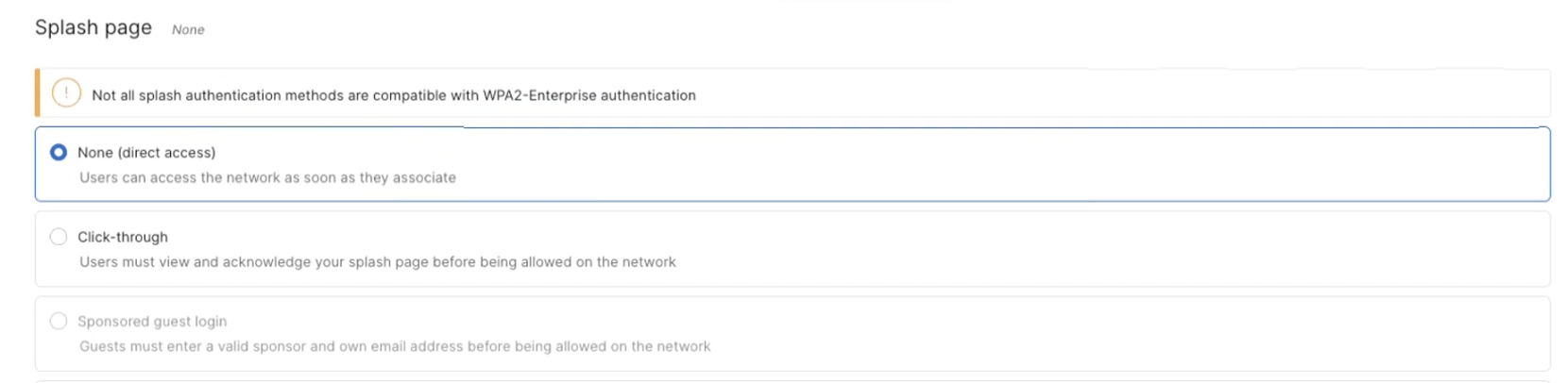
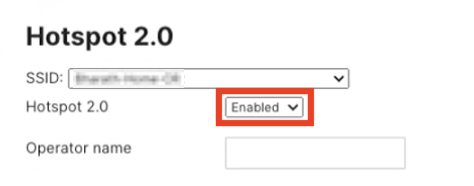
Navigate to Wireless > Hotspot 2.0 to ensure Hotspot 2.0 is enabled:
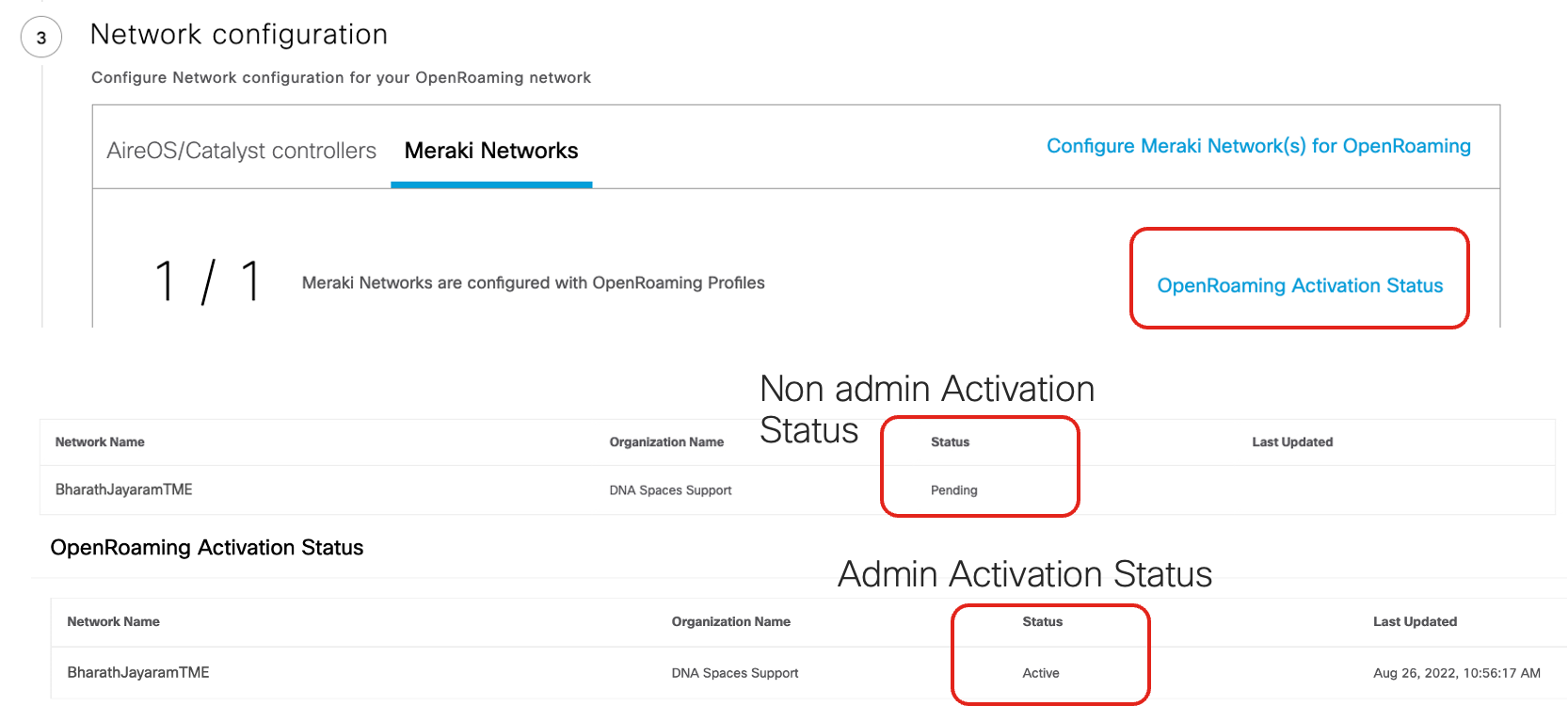
Check Activation
Check the OpenRoaming activation status on Cisco Spaces dashboard:
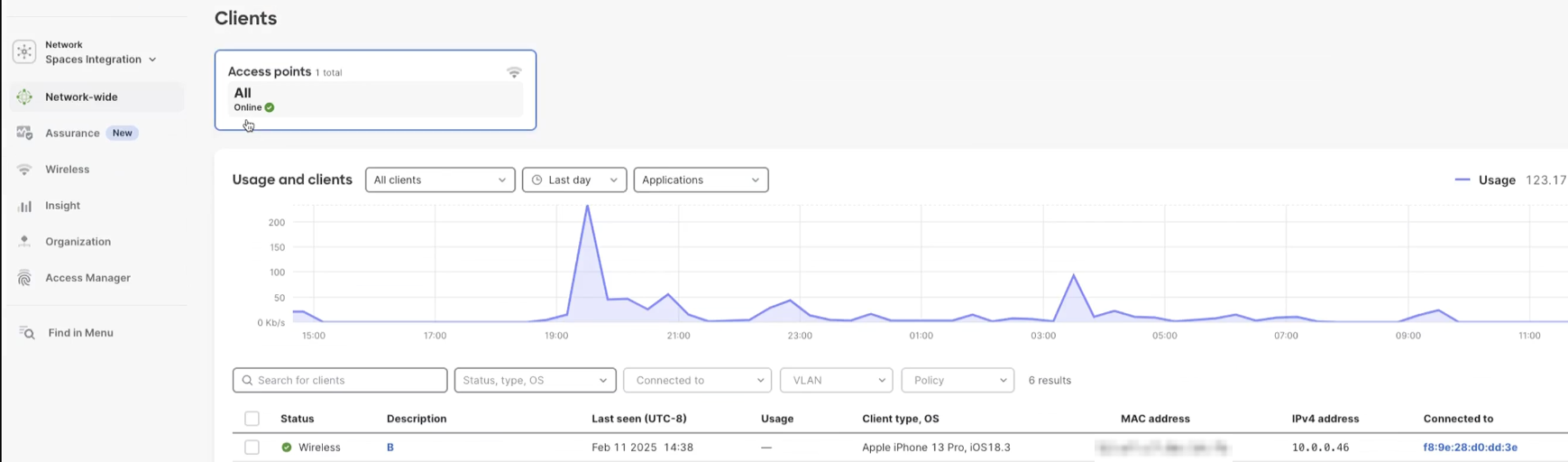
If using Meraki, you can check client connection by navigating to Network-wide > Clients. Check the device is connected.
Test Your OpenRoaming Network
You can test your OpenRoaming network configuration through the following methods:
Cloud/Social: To use this method, download the OpenRoaming mobile app from the iOS App Store or Google Play Store to your mobile device.
Device Manufacturer: Use this method to test your OpenRoaming network natively on a Samsung or Google mobile device.
Other Methods: In addition to the above two methods, you can also test your OpenRoaming network using the following two options:
Carrier Offload: If you have set up a Carrier Offload solution, a mobile phone from the supported carrier will automatically get attached to your OpenRoaming network.
Cisco Spaces SDK: If you have integrated your brand’s mobile app with Cisco Spaces SDK, a mobile phone with your mobile app will automatically get attached to your OpenRoaming network.
For more information about Cisco Spaces SDK, see https://developer.cisco.com/docs/dna-spaces-sdk/. Log in using your Cisco credentials, if prompted.
View OpenRoaming Reports
To view your OpenRoaming reports, click > Home.
The following reports are available in the OpenRoaming dashboard:
Unique Devices
Devices by IDP
Devices by Manufacturer
Data Usage
Average Visit Duration
Data Consumed per User
Connections per Day
Connections per Hour
APPENDIX
Enable Hotspot on Cisco Spaces Connector 2.x
Cisco highly recommends using Spaces Connector 3.x. But if Hotspot needs to be enabled on Spaces Connector 2.x, follow the steps in this section.
Click here for a video guided demo [From 2:35min]
In the OpenRoaming window, click Set Up OpenRoaming or choose
 > Setup.
> Setup.
If you have completed the OpenRoaming Profile configuration as per the previous Step 1, click Continue OR Setup in the configuration wizard to proceed.
The OpenRoaming Setup window is displayed.
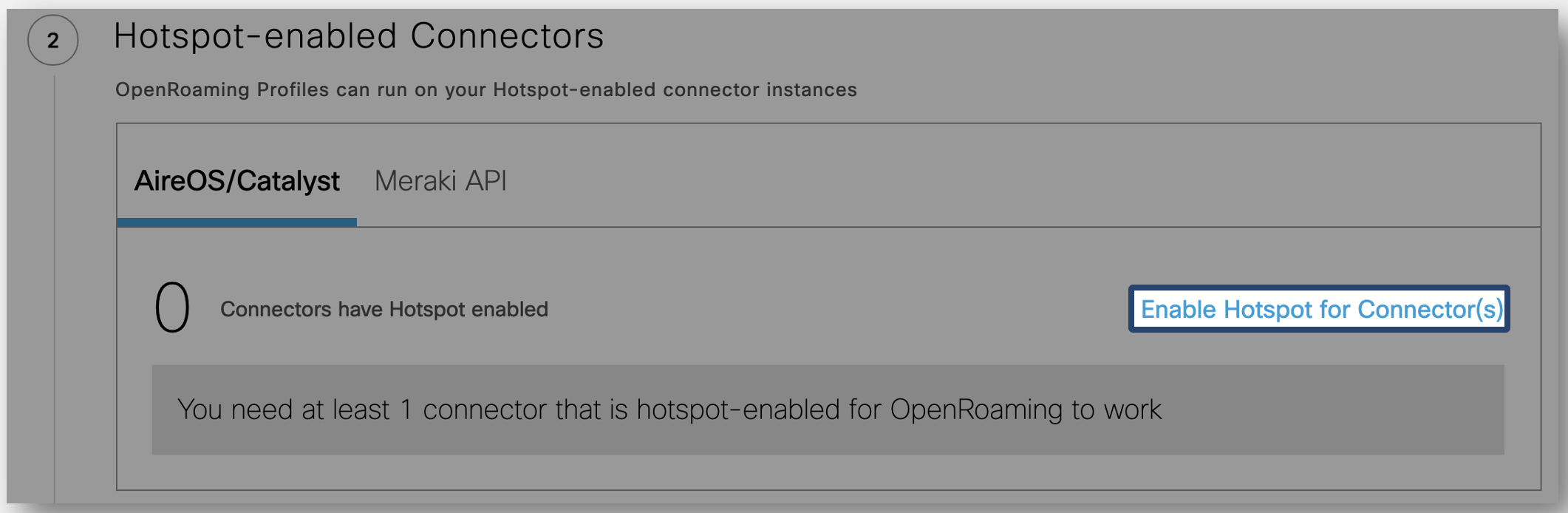
A list of all the Cisco Spaces Connectors, along with their status is displayed in the Hotspot-enabled Connectors section.
Under the AireOS/Catalyst tab, click the Enable Hotspot for Connector(s) link.
The OpenRoaming - Add Hotspot window is displayed.
Enable Hotspot for Connector(s)
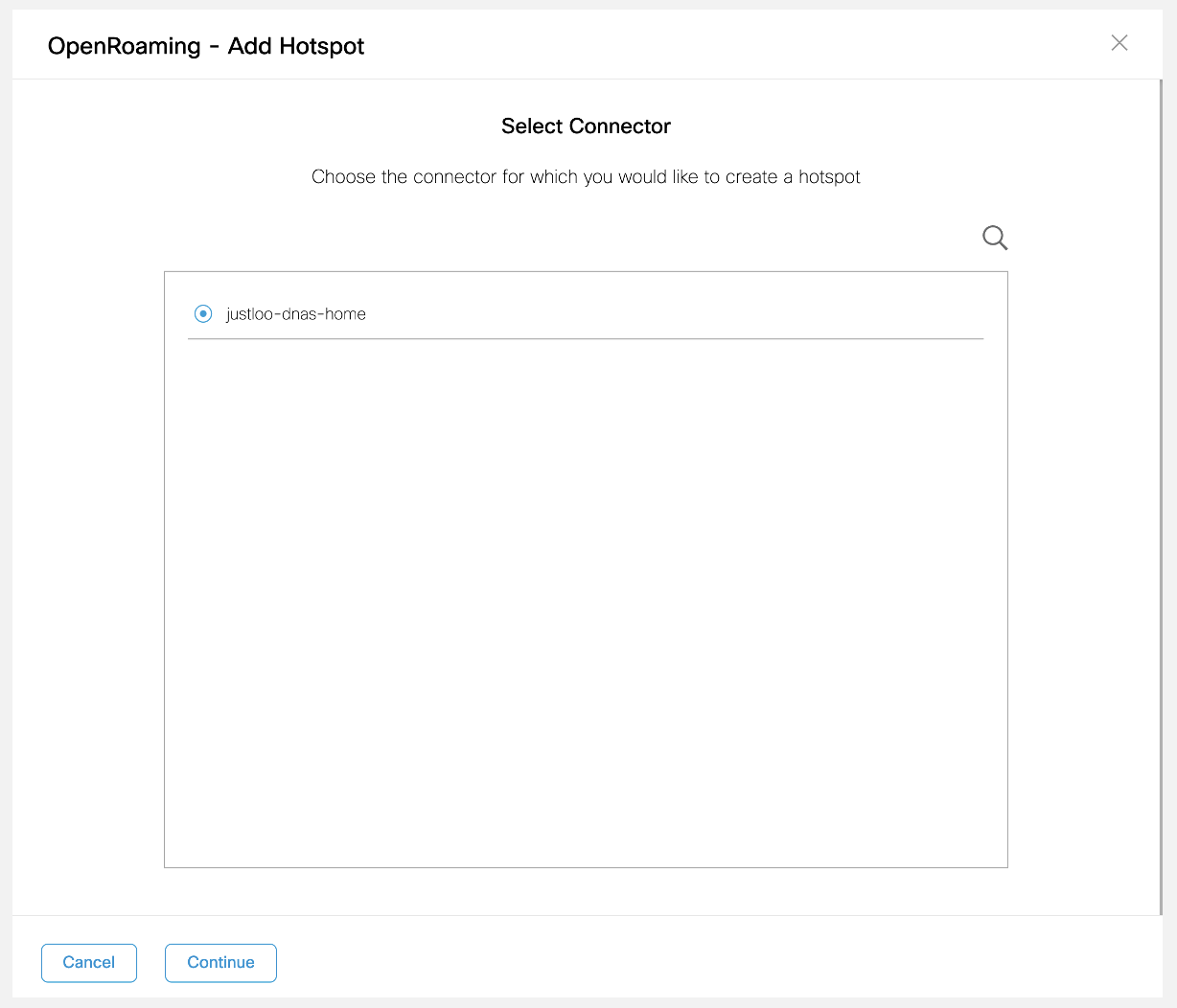
Select the Cisco Spaces Connector for which you want to enable the hotspot and click Continue.
Select Connector
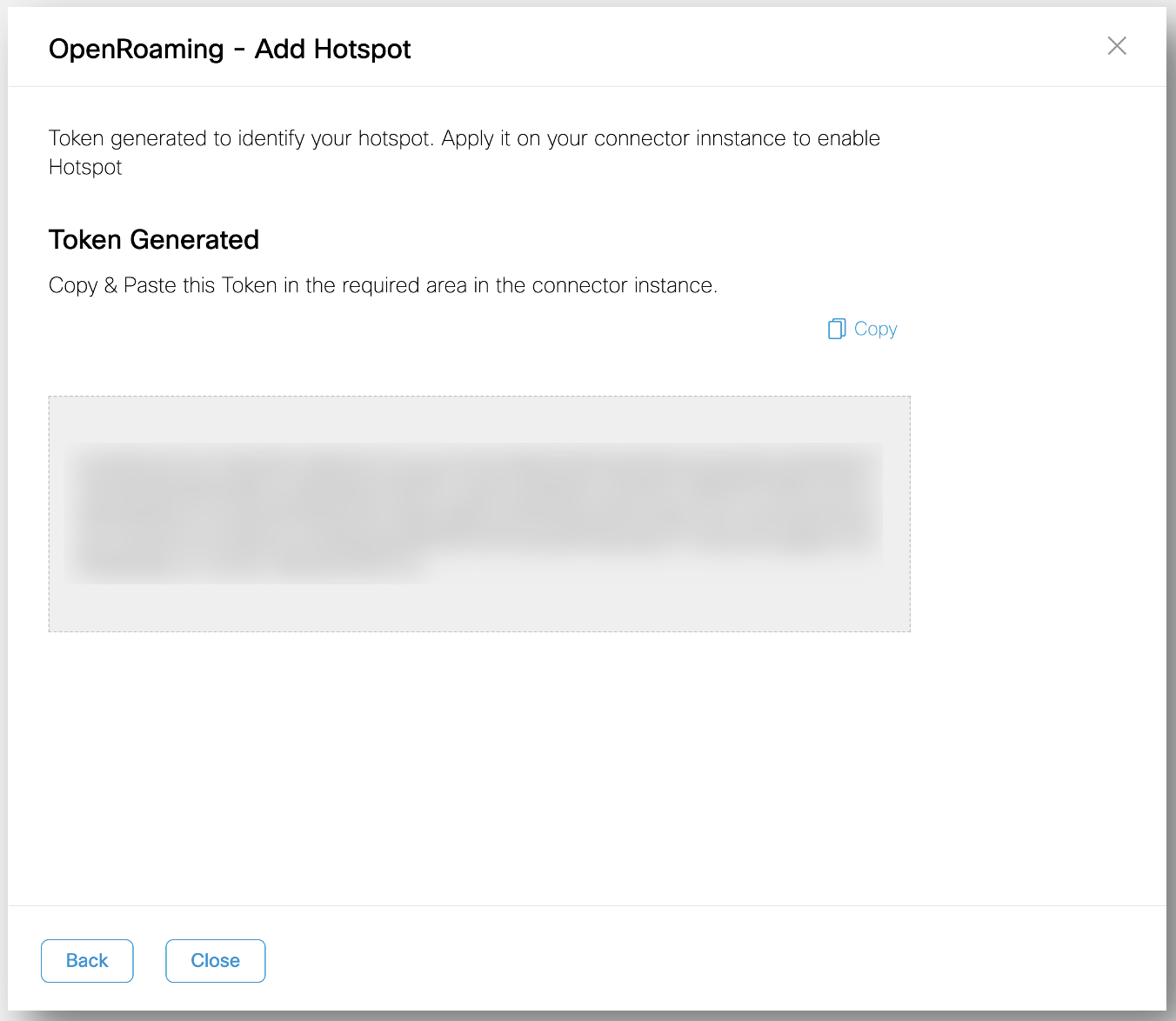
A token is generated, and a Hotspot created successfully message is displayed. This token is used by the Cisco Spaces Connector to download the hotspot connector container.
Under Token Generated, click Copy.
Copy & Paste Generated Token
Go to the web interface for the Cisco Spaces Connector
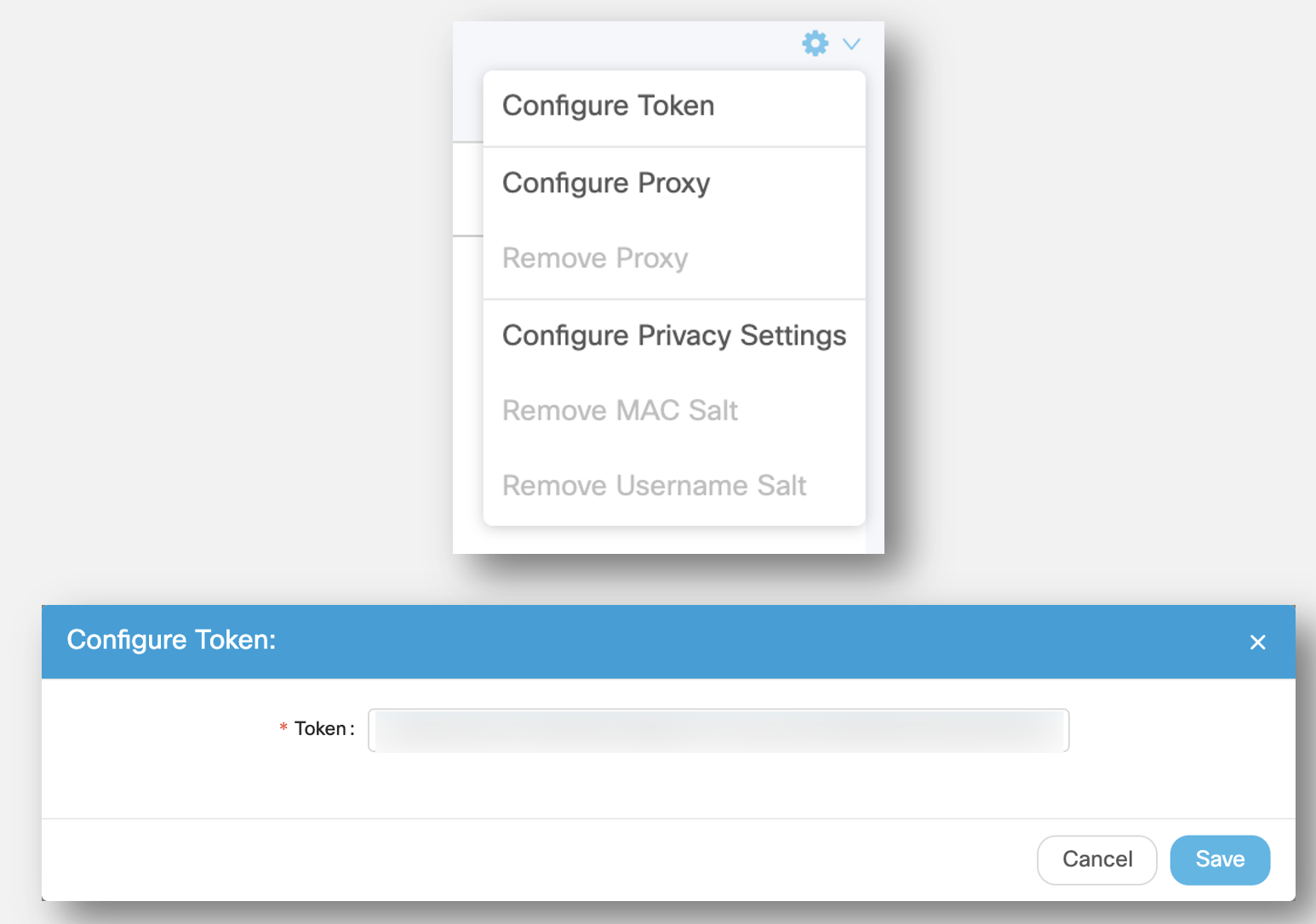
Click the Gear Icon and select Configure Token
Paste this token in the Configure Token window of the Cisco Spaces Connector GUI.
Configure Token in Cisco Spaces Connector GUI
Note that a token can only be used once for a single Cisco Spaces connector.
If a token is used more than once, the hotspot-enabled connector will not work. If the connectors are in active-active mode and share a connector token, you will need different hotspot tokens for each connector.
Click Save.
The Connector will then download and install the Hotspot Connector image.
When a new software version of the hotspot container becomes available, the DMS service will notify the connector, and the connector will display the availability of the new software release in the connector UI. The upgrade process mirrors the process of a new install, except that no token configuration is required because it is already configured. Upgrade is a single click. The Connector downloads the new software release, stops the old container, and starts new container.
Refresh the OpenRoaming Setup window.
The new hotspot-enabled connector is now displayed in the listing in the Hotspot-enabled Connectors section. In the Hotspot tab, verify the status of the hotspot-enabled Connector. If the status is Running![]() , it indicates that the OpenRoaming hotspot has been successfully enabled for the Cisco Spaces Connector.
, it indicates that the OpenRoaming hotspot has been successfully enabled for the Cisco Spaces Connector.
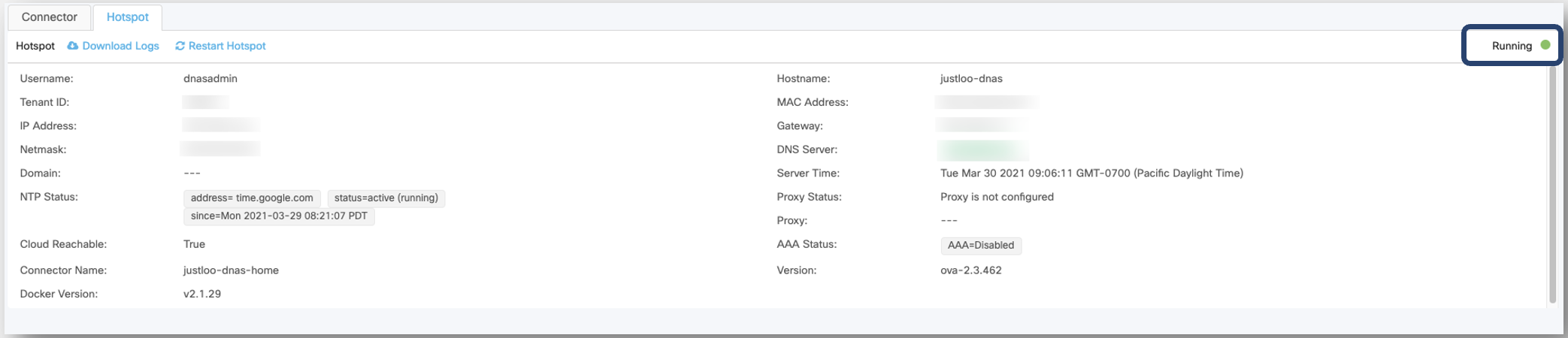
Hotspot enabled on the Connector
REFERENCE
For more information about OpenRoaming in a Cisco Spaces setup, see the following documents:
For all Cisco Spaces documentation, see:
https://www.cisco.com/c/en/us/support/wireless/dna-spaces/series.html
